Security
Working With Driver: Your Security, IP, Copyright, and Legal Questions Answered
Driver prioritizes your security, IP protection, and compliance needs at every stage, offering flexible deployment options and a commitment to data privacy and legal standards.

Adam Tilton
October 30, 2024
Onboarding your organization to Driver offers significant opportunities to accelerate your understanding of legacy code, port software to new hardware, reduce product time-to-market, and streamline engineer onboarding. We understand your team may have questions about using a generative AI tool like Driver, particularly regarding deployment, security and compliance, IP protection, copyright, and more. Here, we address the key questions we most frequently receive from customers.
TLDR: Driver prioritizes your security, IP protection, and compliance needs at every stage, offering flexible deployment options and a commitment to data privacy and legal standards.
How Driver Works
At Driver, we harness Large Language Models (LLMs) to write detailed documentation from source code and enable interactive experiences for exploring source code assets. Driver is meticulously crafted to ensure a seamless, secure, and efficient integration with your existing codebase. Here's a detailed overview:
Connecting to Your Codebase: We utilize advanced encryption protocols during data transfer, ensuring your code remains confidential as it moves from your repositories to our platform.
Chunking Code into Smaller Pieces: By segmenting the code into smaller units, we ensure a granular level of analysis. This not only enhances the accuracy of the documentation but also minimizes the exposure of any single piece of your software.
Sending Code to LLMs: The segmented code is processed by LLMs in a secure environment, isolated from external threats.
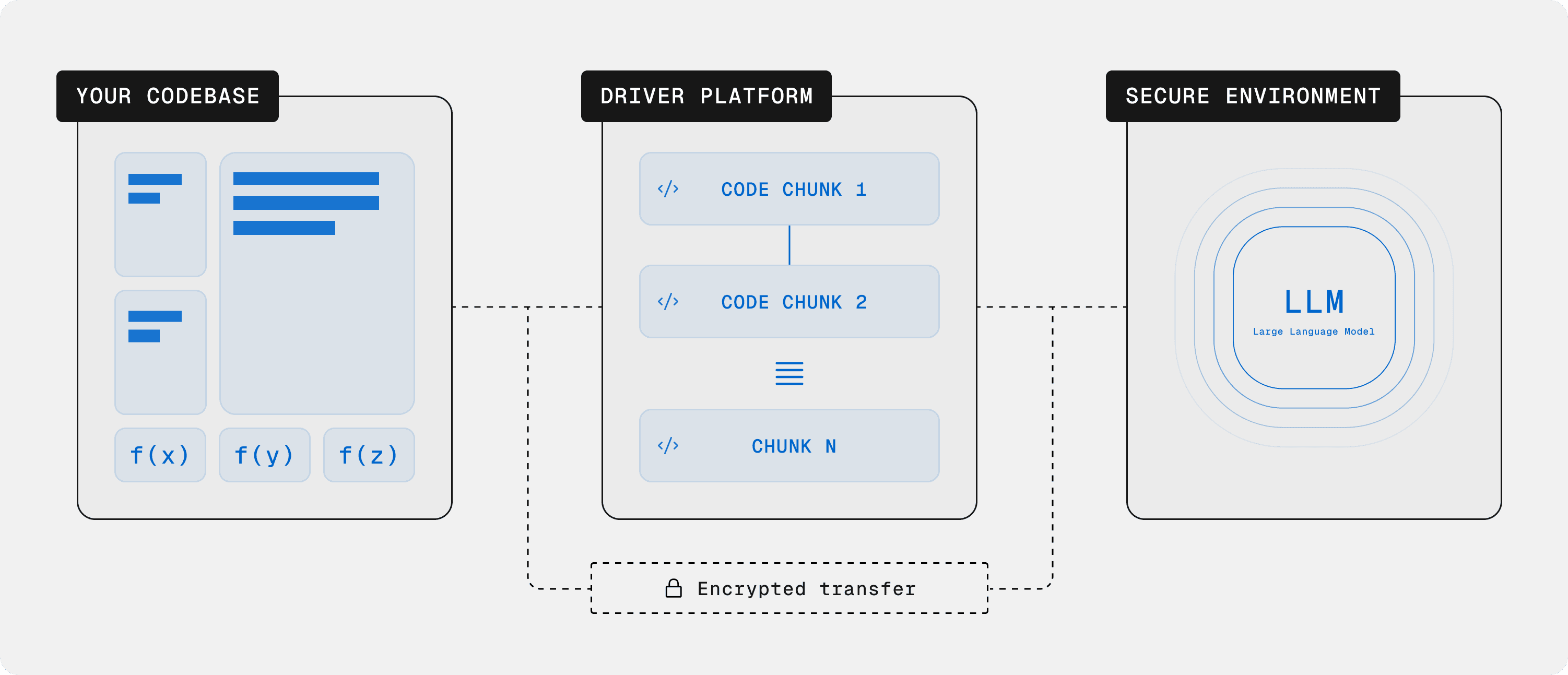
Illustration of how code flows through Driver AI's platform, from initial encryption during transfer to granular segmentation and final processing by Large Language Models (LLMs) in a protected environment.
How Driver is Deployed
Driver offers multiple deployment options to suit your specific security needs and infrastructure requirements. Typically, customers begin with our multi-tenant managed service and scale with our single-tenant managed service.
Multi-tenant Managed Service
Our default offering provides a cost-effective, rapidly deployable solution:
Secure hosting with strict data isolation between customers
Quick setup and immediate access to the latest features
Available in both US [and EU] regions for data residency and compliance purposes
Optional Enterprise SSO capabilities for seamless integration with your existing authentication systems
Single-tenant Managed Service
For organizations requiring an extra layer of isolation:
Dedicated AWS account, infrastructure, and data storage for your organization
Enhanced security with the option for PrivateLink connectivity
Choice of US or EU regions for data residency and compliance purposes
Ideal for enterprises with stringent data isolation requirements
FAQ
Can you meet enterprise security/legal requirements?
Yes, Driver is designed to meet enterprise security and legal requirements through flexible deployment options tailored to your security needs.
With our multi-tenant managed service, you benefit from secure hosting with strict data isolation and options for enterprise SSO and data residency in the US or EU, all in a cost-effective solution.
For organizations with stricter data isolation needs, our single-tenant managed service provides a dedicated AWS environment with isolated databases, PrivateLink connectivity, and dedicated authentication controls, also available in US and EU regions. This setup ensures a high level of data separation and is ideal for enterprises with stringent security requirements.How do you handle different data classification requirements?
Driver handles different data classification requirements by offering a flexible deployment approach that aligns with your security needs as they evolve. Typically, customers begin with our multi-tenant managed service. As security requirements grow, customers can scale to our single-tenant managed service. This setup supports enhanced data classification needs with complete control over data handling, storage, and transmission, which is ideal for organizations with stringent data separation and regulatory requirements.
Driver's Comprehensive Security Framework
At Driver, we've carefully crafted our security framework to address the intricate challenges and stringent requirements of enterprise-level security.
SOC 2 Type II Compliant
Driver is SOC 2 Type II compliant. This means we have a long list of security protocols in place, including data encryption, access controls, and continuous monitoring. These and more are described at trust.driver.ai. We also support our customers’ specific security requirements through different deployment models, which allows us the flexibility to meet your more specific needs.
FAQ
How is our proprietary code protected?
Your proprietary code is protected through strict access controls, data encryption during transfer and storage, and continuous monitoring for any unauthorized access, all of which are part of our SOC 2 Type II compliance protocols.What are the guarantees around data privacy?
We consistently monitor and enforce privacy standards to prevent unauthorized access, ensuring that sensitive information remains confidential and protected in line with industry best practices.Are there protections against code and IP leakage?
Yes, we have protections against code and IP leakage, including secure access controls, encryption during data transfer, and stringent monitoring for unauthorized access or unusual activity.
Intellectual Property Protection
We understand that your software's intellectual property (IP) is more than just code—it's a representation of your organization's innovation and competitive advantage. Our commitment is to safeguard this IP, ensuring it remains confidential and uncompromised throughout our engagement. We do not use your IP to train or otherwise improve large language models.
FAQ
How do you handle AI model training? Is our code used to train models?
No. We do not use your IP to train large language models.Can you assure us that the generated documentation doesn't infringe on any existing copyrights?
Yes. The output of Driver is an analysis of our customers’ code base. That summary is generated by analyzing the customers’ code (which the customers license us to analyze). We do not copy the content of the analysis from any third party, nor do our customers. Copyright prohibits copying without permission, and since neither we nor our customers copy the analysis, there’s no copyright infringement. We stand behind our products and offer our customers an indemnity if there are any claims that our platform infringes. The indemnity is in our MSA.
Build with Confidence and Peace of Mind
Driver provides a robust, secure platform designed to support your organization’s growth while ensuring that your security, intellectual property, and legal requirements are met at every stage. With flexible deployment options, SOC 2 Type II compliance, and a commitment to data privacy, Driver is well-equipped to handle the complexities of integrating AI with proprietary code. From our cost-effective and secure multi-tenant managed service to our isolated and customizable single-tenant solution, we prioritize your data’s safety, privacy, and compliance needs. We respect your IP by keeping it entirely separate from model training and providing indemnity for any potential copyright concerns.
We also understand that security requirements evolve over time. We are open and prepared to meet any additional security requirements your organization may have to ensure complete alignment with your security standards. At Driver, we are dedicated to being your trusted partner, helping you unlock the full potential of AI with unwavering confidence and peace of mind.

